Solution
NIS-2
Our cloud-based risk platform is tailored to help you comply with the Network and Information Security Directive 2 (NIS-2) with efficiency and ease.
3 challenges
#1. Third-party risks
Keeping an overview of the entire third party landscape is not simple, but essential considering evolving threats and emerging regulatory compliance requirements such as NIS-2. Many organisations struggle to promptly identify, assess, manage and monitor (third-party) risks.
#2. Stakeholder engagement
Engaging internal teams with risk management and internal control activities, such as risk profiling, control testing or assessment reviews, can be challenging due to a lack of understanding, inadequate communication, resistance to change or tool fatigue.
#3. Compliance workload
In today's fast-paced and highly competitive labor market, securing risk professionals can be both challenging and expensive. This is especially true as organisations grapple with challenges across various risk domains, striving to mitigate emerging risks and manage the rising number of requirements.
Key benefits
- Align with best-practices
- Streamline processes
- Improve stakeholder engagement
- Standardise reporting
- Improve decision-making
3 common challenges
and our solutions
#1. Third-party risks
Keeping an overview of the entire third party landscape is not simple, but essential considering evolving threats and emerging regulatory compliance requirements such as NIS-2. Many organisations struggle to promptly identify, assess, manage and monitor (third-party) risks.
#2. Stakeholder engagement
Engaging internal teams with risk management and internal control activities, such as risk profiling, control testing or assessment reviews, can be challenging due to a lack of understanding, inadequate communication, resistance to change or tool fatigue.
#3. Compliance workload
In today's fast-paced and highly competitive labor market, securing risk professionals can be both challenging and expensive. This is especially true as organisations grapple with challenges across various risk domains, striving to mitigate emerging risks and manage the rising number of requirements.
Our features to simplify & automate compliance

Register internal and external risks. Link risks to a specific third-party, internal control(s) and/or location within your organisation. Follow the ISO 31000 best-practice workflow containing of risk identification, assessment, treatment and monitoring. Use the interactive risk matrix to easily filter different risk disciplines and scores.

One integrated register for all your third parties. Register multiple contracts per third-party. Assign risk profiles to segment your landscape, taking into account multiple risk domains such as cybersecurity, sustainability and compliance. Connect with your procurement system to retrieve and enrich your supplier data.

One integrated register for all your internal & external compliance requirements Use it to manage compliance requirements for security, sustainability, privacy, legal, quality and many others. Define a specific scope & applicability per compliance requirement and link them to one or more assessment questionnaires. Monitor compliance in real-time.

Integrate the different third-party assessment efforts of all your risk and compliance disciplines. Combine questionnaires from different risk disciplines into one third-party assessment. Suppliers log in to a secure supplier portal in which they can collaborate and provide their evidence. Our AI-powered review module makes an initial analysis.

Continuously monitor your third-parties in 2 million news sources and receive instant alerts on negative news articles. Activate our out-of-the-box integrations with BitSight, SecurityScorecard, Ecovadis, Refinitif and many others to retrieve your third-parties' security, sustainability, financial or compliance risks ratings in one central overview.
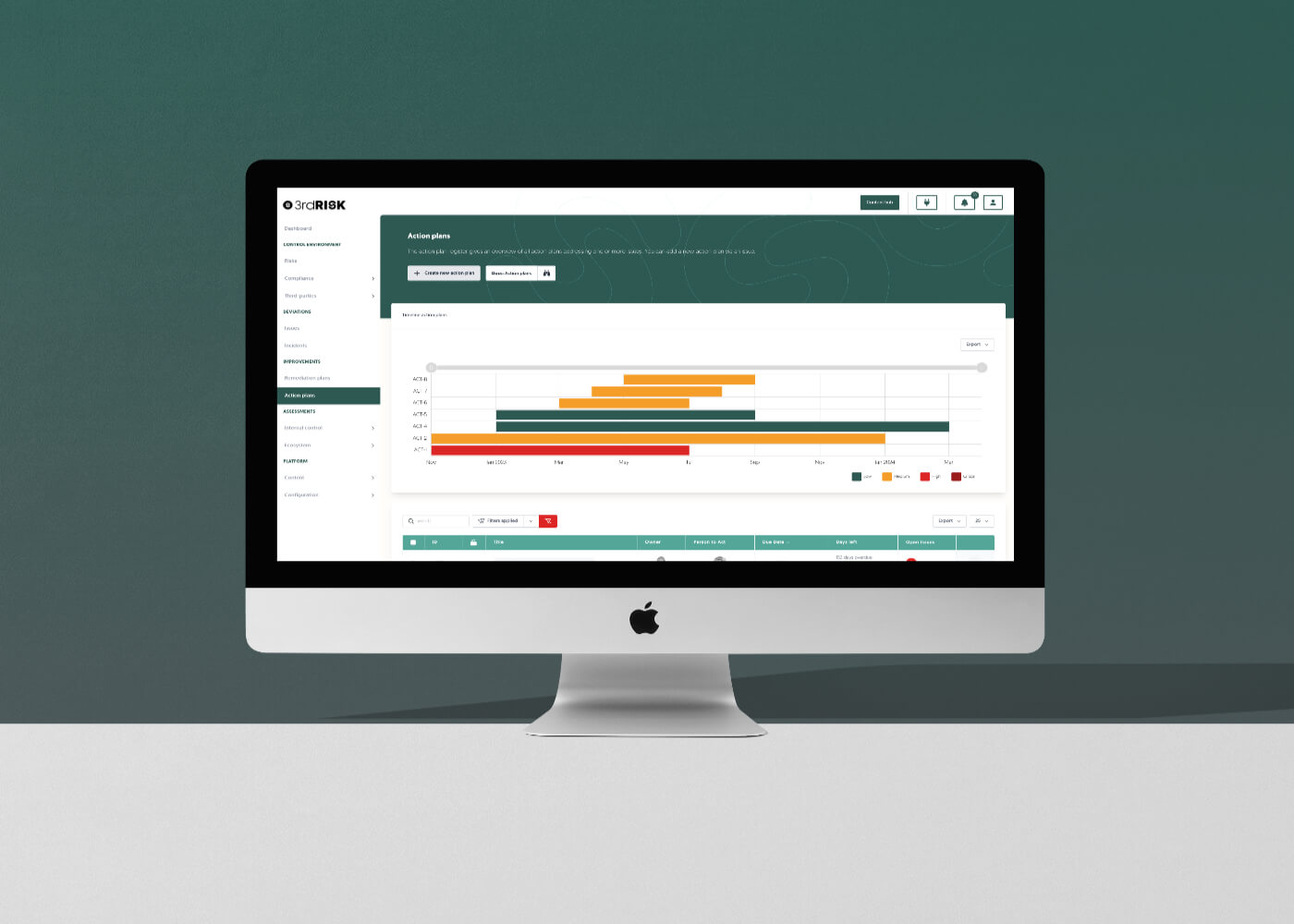
Consolidate remediation actions across all internal teams and third-parties within a unified action plan repository. Assign ownership through our platform and Microsoft Teams. Set and adjust timelines for each action, with reminders to keep progress on track via our platform's virtual officer, e-mail and Teams. Visual indicators offer status updates, simplifying oversight.

For organisations with limited time or resources for third-party risk management, we have formed partnerships with esteemed experts in the field. These partners can fully manage the entire third-party risk management process for you, encompassing risk profiling, due diligence, and real-time monitoring, by using our fit-for-purpose platform. Schedule a conversation.
NIS-2: What will it mean for you? (Update 2024)
Tackling the growing challenge of third-party cyber due diligence
Starting with third-party risk management (1): How to set up your capability?
FAQ
In the overview below, we have listed the most frequently asked questions and answers. Do you still have questions? Just reach out to one of our experts.
Can I effectively manage third-party risks with 3rdRisk without a dedicated team?
Yes. By using our third-party risk platform, you can already assess and monitor up to 100 third parties with only a few hours a week. In addition, you can also decide to outsource third-party risk management activities. For organisations that are inclined to outsource these tasks, we have established partnerships with renowned partners who are well-versed in leveraging our platform’s capabilities allowing them to deliver excellent quality at a competitive price.
Do I need training to operate the 3rdRisk platform?
No. No training or certification is required to operate the 3rdRisk platform. For organisations that choose to manage their third-party risk management program in-house, our platform acts as an intuitive platform, streamlining processes and making follow-up and monitoring straightforward. Its design ensures that teams can quickly familiarise themselves with its features, reducing the learning curve and allowing for immediate implementation.
Why should I comply with NIS-2?
For organisations that fall under NIS-2, compliance is a critical task. Non-compliance with NIS-2 could result in substantial fines, up to 2% of the annual turnover. More importantly, adhering to NIS-2 guidelines is essential to ensure digital security and prevent cyberattacks. NIS-2 mandates organisations to elevate their digital security and adapt to the growing threats of cybercrime.
What sectors are in scope of NIS-2?
NIS-2 targets entities operating in critical sectors such as energy, transportation, healthcare, and financial services, but also other sectors crucial to the ongoing function of the economy and society:
- Healthcare
- Transport
- Digital infrastructure
- Water supply
- Energy
- Digital service providers
- Data centers
- Providers of public electronic communication services
- Water management
- Manufacturing of medical devices and chemicals
- Food
- Space
- Postal administration
- Public administrations
What is NIS-2?
NIS-2 legislation builds on previous NIS regulations and aims to enhance the security of network and information systems within the European Union. This requires member states to identify and implement appropriate security measures. The primary objective? Reduce cyberattack risks and limit their impact.
Does 3rdRisk integrate with procurement systems?
Yes, our platform has (API) integrations with the most commonly used procurement system, like SAP ARIBA, S4/HANA, Coupa and Oracle.




.svg)
